Solana fell from a proof-of-stake leader to an unstable, frequently offline chain that has been the target of high-stakes, high-profile hacks.
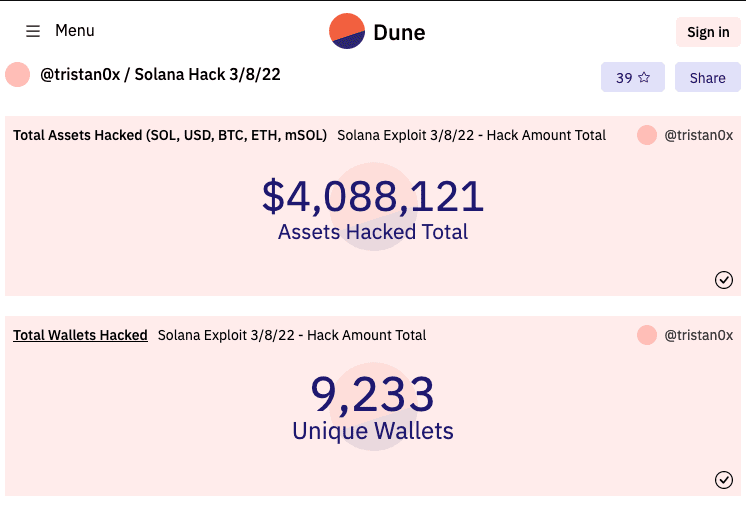
On Aug. 2, an exploit related to the chain exposed 9,233 wallets to a hack that sucked in $4 million of value from users‘ fingertips.
Two days later, on Aug. 4, the decentralized Solana foundation blamed the outbreak on a security flaw within the Slope browser wallet, a popular Solana solution similar to MetaMask purpose-built for the Web3 community. Every exposed account had either used or had a connection to Slope.
Slope then released their report, admitting they recognized a security breach but claimed no responsibility, stating there was no evidence tying the fault to the loss of Solana funds.
The Slope team said that a third-party app was saving wallet seed phrases and sensitive data “in cases where the apps generated an error event.”
According to Solana, these seed phrases, copied over from Phantom wallet or created within Slope, were used to access users’ funds over four hours.
Solana stated that neither block creation nor any other aspect of the chain was affected, aside from the drained custodial wallets.
The bad news came after a complete chain shut down in June, followed by a programmer spoofing the entire chain’s total value locked (TVL).
What do industry experts think?
Web3 adoption appears inevitable to industry observers, but each passing block brings news of shuttered exchanges, hacks, and deceit.
Nikos Andrikogiannopoulos, CEO of crypto chain tracking firm Metrika, said the multi-chain world’s fast pace of software upgrades would inevitably introduce more vulnerabilities, so it is only natural for exploits to pop up.

“Effective monitoring infrastructure in the hands of the community acts as a powerful deterrent to bad actors,” he said. “Similar to weather alerts that get communities mobilized, evacuate threatened areas, and activate volunteer rescue teams, blockchain communities need processes and tools to deal with emergencies.”
Daniel Keller, Co-Founder of Web3 cloud infrastructure firm Flux, concurred, saying that disruption is volatile.
“Most of the developers in the blockchain space are learning on the fly, as they come from conventional technology stacks and are retrofitting their skills,” he said.
For decentralization to take over, education will have to become a driving force for better and more secure programming.
Tech is not born
“Technology is not born but instead developed, and as adoption grows, you will see a robust push from leadership driven by the institutional demands for their client base, he said.
“DeFi needs to feel like legacy finance but function like a decentralized network, and for this to happen, we need to be good stewards of speed and security best practices.”

They already doubled the total value locked of the network by spoofing numbers, CoinDesk investigators allege. CoinDesk reported that an unpublished blog post allegedly drafted by Saber stablecoin creator Ian Macalinao amounted to a confession that $7 of the $10 billion TVL in Solana was faked by double-counting assets.
Macalinao has not responded to CoinDesk regarding the allegations at the time of their publishing of the investigative report. Fintech Nexus News has also requested a comment from Solana, with no response as of this article’s original publishing Tuesday.
The Nomad hack and cross-chain vulnerability
The hack came a day after a $400-million attack hit the cross-chain coin transfer protocol Nomos bridge.
A crypto bridge connects currencies with an exchange rate. A bridge is either a custodial or decentralized mechanism that takes input cryptocurrencies and outputs other “wrapped” cryptocurrencies. For example, send Nomos bitcoin to “change” for eth, and the protocol would output wrapped bitcoin on the ethereum chain.
Bridges have historically been the target of hackers.
Andrew Morfill, Chief Information Security Officer at coin custodian Komainu, said looters pillage until security can stop them.
“As the industry matures, we will continue to see hacks. From early indications with Nomad, it’s clear that opportunistic looters drove it. Still, nation-state threat actors have targeted cross-chain bridges in the past with meticulous planning and precise execution,” Morfill said. “The drivers are different, but the outcomes, inevitably, are the same…loss of assets.”

Andrikogiannopoulos said that cross-chain is complicated, and with every update comes more bugs to exploit. He explained that the bug the Nomos hackers used was a relatively simple one to understand.
“In the case of Nomad, a bug in the software update allowed a type of transaction that normally should be allowed to only the owners of the funds,” he said. “This bug allowed anyone who wanted to copy-paste the transaction type, change the recipient’s address, and drain the funds.”
Keller said most of DeFi still relies on a centralized infrastructure.
“Blockchain was created to do one thing, allow movement without a trusted third party. Most of the current DeFi models use a hybrid of centralized and decentralized technology, so there is an increased risk of exploits and malicious third-party actors,” he said.
“Attention needs to be given to security and not just the speed of development as we push DeFi products to the masses.”
What can the industry do to prepare for the next breach?
While hacks are not new, even for Solana, they have amounted to the most significant losses of funds in cryptocurrency, Morfill said.
“In terms of prevention, an industry set of standard smart contract templates known to be secure, smart contract auditing, and secure software development lifecycles would be steps in the right direction,” he said.
Keller said most of the DeFi experts come from traditional finance, and when they build, they focus on speed, Flash Boys style. Of course, he recommended builders flock toward “more secure” infrastructure, like his firm Flux offers.
“Most decentralized finance makeup is refugees from conventional finance, focusing on building a legacy-based system on DeFi,” he said. “When these leaders, developers, and teams focus on iteration, they look at the mechanics and development for speed and quick access; security tends to be an afterthought.”
Fraud checks come after
Andrikogiannopoulos said, unfortunately, a lot of fraud detection comes after the breach when the industry needs a coordinated response at the time of the attack. Like an immune system response, analytics and action need to happen immediately or even before the launch of the attack.
“Many of these exploits start with small experiments, often in TestNet, and later get fully deployed on MainNet. Real-time detection can raise alerts on suspicious activity before these exploits get “into production,” he said.
For example, in the Nomos hack, a transaction with an empty or zero hash executing on the chain should have raised immediate red flags and launched an automated quarantine system. Today, he said that these fixes are ad hoc and community-based when they should be industry automatic and enforced.
“After an exploit goes live, the entire community should be alerted in real-time and quickly and allow for quick community response, like freezing of the exploited funds, coordinating with validators to pause network activity while a patch is prepared,” he said. “There needs to be more tooling and infrastructure in this direction to empower the entire community with a standardized response to emergencies.”


