As more workplaces embrace cloud technologies and the prospect of remote working, the instances of ransomware attacks have increased.
In the first half of 2021, there were 304.7 million ransomware attacks globally, a 151% increase since 2020. This follows an upward trend since 2018.
Although ranked as a lower cause for concern than viruses and trojans, ransomware is a significant contributor to the high-level risk of cybersecurity on the register of institutions. Problems revolving around data leakage, privacy, and operational disruption are just some of the many issues that can arise, destroying reputations and resulting in legal exposure.
“Just as the cloud has been a massive enabler for organizations for digital transformation, it’s having the same benefit to the attackers,” said Matt Walmsley, Senior Director at EMEA, during a webinar for Lookout. “This means that we’ve seen almost a professionalization of ransomware crews. They now offer ransomware as a service.”

He explained that the cybersecurity sector is starting to see ransomware groups distributing their services, making instances more prolific. The approach has also changed, with groups denying access to data and stealing and leveraging it to ensure payment.
“These are rational criminals who want to monetize the opportunities they have from attacking you. They’re even offering value-added services,” he continued. These “value-added services” could include, as well as returning unencrypted data upon payment, explaining how they entered the system and implemented the malware. “They’re almost offering you a nefarious penetration test report about how you got turned over.”
Ransomware attacks becoming part of daily grind
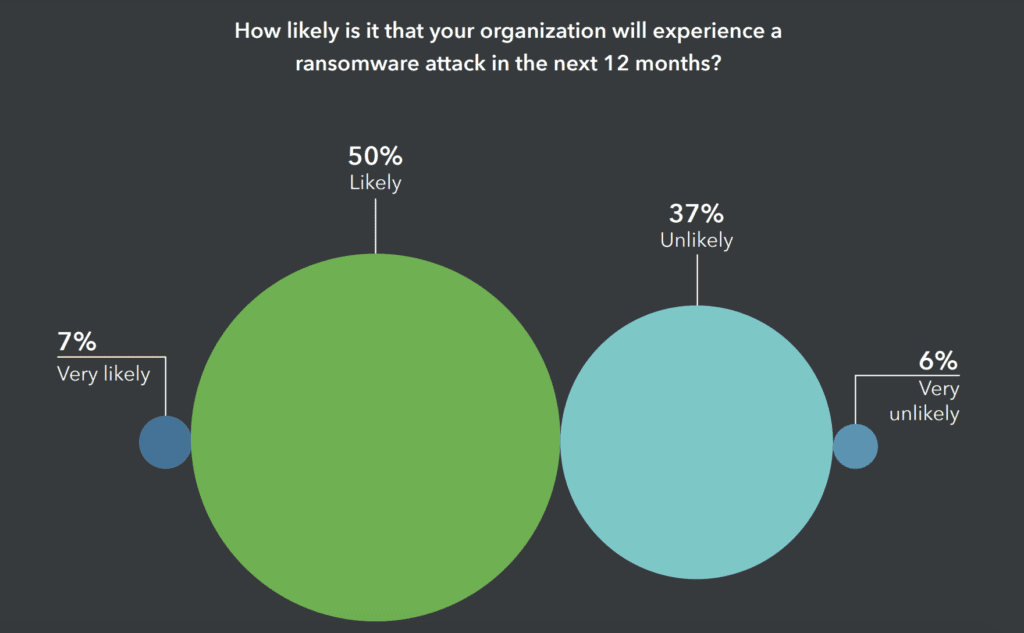
In a study carried out by Lookout, in association with Pulse, they found that 71% of respondents had worked in an organization that had experienced a ransomware attack. In addition, 45% of business leaders consider ransomware payments an operating cost.
In 2021 the world saw some major ransomware attacks on prominent international businesses. Victims included Apple, Accenture, the Colonial Pipeline Company (CBS), and JBS, each responding to demands of millions of dollars.
The CBS hack caused massive disruption to the company’s supply chain, halting fuel distribution for five days. The attack group, Darkside, gained access to the CBS billing system through the use of stolen employee data which they used to gain access to the VPN, which did not have multi-factor authentication. They could access many elements of the business’s virtual network through the VPN.
“Ransomware isn’t a single thing,” said Walmsley. “Ransomware is something that has multiple stages. The attacker has to achieve a whole lifecycle of techniques, tactics, and procedures.”
“Sometimes, we don’t always know the initial attack. I’ve been aware of attacks where the attacker has had a foothold for many months. While the ransomware encryption and the ransom note are the most overt thing, it’s certainly not the first thing that happens.”
Movement to cloud-based ops could create vulnerabilities
“Increasingly, as we move to the cloud, things like identity and credentials become the key to gaining initial access,” he continued. “They pivot from endpoint over to the cloud. And that impacts our own security practices and controls because often, organizations will often have disparate policies and controls between endpoint and cloud services. There are visibility and detection gaps. Some of those devices I use to access my legitimate cloud services may not even be managed.”
“When we look at the different types of cloud adoption, compared to traditional on-premises security and operations, the demarcation between responsibility for the physical infrastructure, the applications, the OS, the network controls the identity and Directory infrastructure, changes based upon our cloud compute consumption model.”
“What doesn’t change, regardless of our consumption model, is that we are always responsible for our information and data for the accounts and identities for the people and entities using those services and accessing those data. And in most cases, we’re responsible for the devices, be the mobile, laptop, or desktop, connecting to those services as well.”
“This move to the cloud means that while that physical perimeter we used to know 10 years ago has evaporated, identity becomes a new perimeter. That’s the place where we need to defend our organization.”
Stages of attack pose multiple points of detection, defense
A ransomware attack comprises various stages, all of which must be successful for the attack to take place. Walmsley explained that organizations have points within these steps where they can take action to avoid a successful attack.
1 – Surveillance and identification of credentials
This is the initial stage where malicious actors will look for points of weakness in access points to the cloud infrastructure. Companies can inspect internet traffic and cloak vulnerable servers from internet discovery while employing a zero trust strategy for remote workers.
2 – Use of credentials to gain entry
After identifying weak points and gaining credentials, the attacker can then use them to access the infrastructure. With the increase of remote workers and many devices to access cloud services, this can be hard to detect. Walmsley recommends implementing a multi-factor authorization protocol and anomalous monitoring log-in activity.
3 – Compromise the existing infrastructure
On gaining access, the attacker can install loader files or software to create a backdoor into the infrastructure. Organizations can detect this if the attacker deletes or renames content as part of this process.
4 – Establish a foothold
The attacker usually creates an auto-start action that remains persistent throughout system reboots to ensure they are not taken out of the infrastructure. Here systems like cloud security can be executed to identify high-risk changes.
5 – Escalate Privileges
The actor will then try to gain access to higher access levels, enabling them to infiltrate the infrastructure further. To avert this, companies can set alerts to be notified as soon as excessive user privileges are detected.
6 – Reduce security Configurations
On gaining access to higher control levels, the attacker can then reduce the security system, allowing them easier access to data and additional levels of the infrastructure. To avoid this, the security admin can set alerts for when settings are changed, and other security measures can be implemented to stop changes.
7 – Discovery
Attacks can sometimes take months, many of which will be dedicated to observing security protocols and practices to properly understand how the infrastructure works and where valuable data is stored. This is usually done through silent, passive tracking and is very difficult to detect.
8 – Lateral Movement
Using this information, the attacker could move around the infrastructure, gaining access to sensitive data. To avoid this, companies can segment access of admins, limiting lateral movement and easy access. This could contain the actors’ access and mitigate the threat of large-scale data theft.
9 – Command and Control
The attacker can open communications with a secondary server to execute the attack. At this time, a lot of the most sensitive data is stolen. Companies can detect this communication and attempt to block it before other back doors are created.
10 – Exfiltration
Additional data is taken as leverage for the impending ransom and used to pressure the victim into payment. “Lock and Leak” steps can also be implemented to increase pressure, leaking some of the compromised data. Content and context-aware signals can help control data downloads and mitigate this.
11 – Lock and Encrypt
This is the final step of the attack, where the attacker executes encryption software and could lock out user access until the ransom is paid. At this point, it is sometimes possible for admins to continue encrypting data over the encryption of the attacker to prevent their entry.

Key takeaways to improve cloud-based security
For Walmsley, there are four key takeaways when addressing the threat of ransomware within cloud technology, aimed at reducing attackers’ opportunity to complete different attack stages.
The initial focus is securing the points where the cloud intersects with the public internet. “??The services edge is tough to define. Detecting risky behavior and security endpoints is crucial to reducing the impact of a ransomware attack,” he said. Additional security at this level could help prevent the attacker from entering the cloud infrastructure and avoid the attack altogether.
The second line of defense could be through making apps and data context-based, allowing limited access based on clues such as location, device type, and risk profile. This is particularly applicable to remote workers.
“VPN still have their place, but the unbridled access they enable can be risky. With users logging in from anywhere, it’s critical to understand the context in which they’re accessing your corporate apps and data and your cloud-based services. This will help you provide the right level of access for a particular app only to the users who need it,” he continued.
In addition, layers of encryption could be added to extracted or modified data, providing additional access security. This may render the data useless to ransomware attackers.
The final point of security is protecting all endpoints, including mobile devices, which have seen a sharp rise in compromising security. “One compromised user or device can be detrimental to the security of the entire infrastructure. The inherent trust we have in smartphones and tablets can make them an attacker’s easiest avenue to exploit,” Walmsley concluded.


